
ExaGrid works with its customers worldwide to include all aspects of security. We drive the majority of our security offerings through talking to our customers and resellers. Traditionally, backup applications have strong security but backup storage typically has little to none. ExaGrid is unique in its approach to backup storage security. In addition to our comprehensive security with ransomware recovery, ExaGrid is the only solution with a non-network-facing tier (tiered air gap), a delayed delete policy, and immutable data objects.
Meet ExaGrid in our Corporate Video
Watch the VideoExaGrid’s Comprehensive Security features:
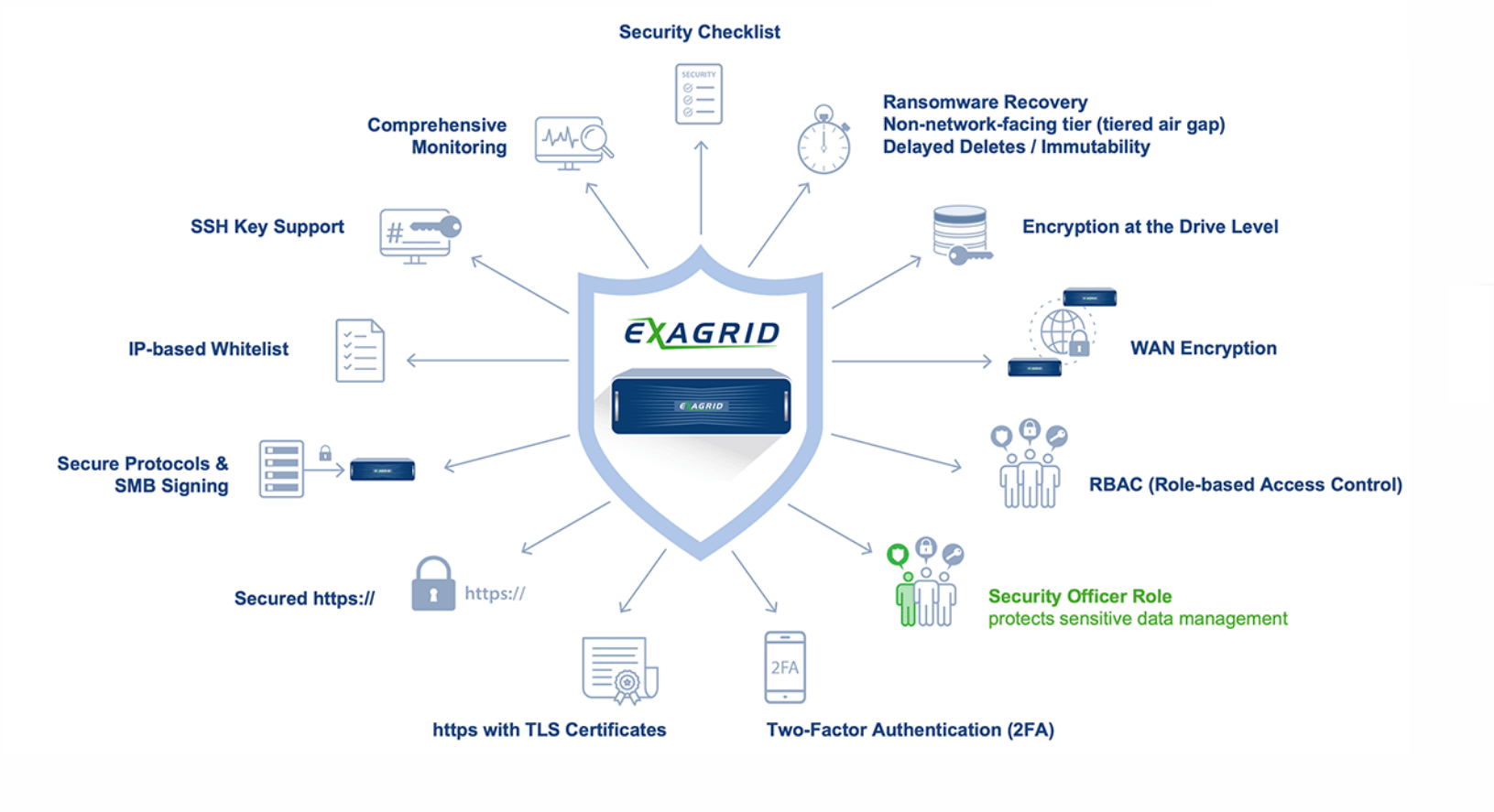
A Closer Look:
- Security checklist for quick and easy implementation of best practices.
- Ransomware Recovery: ExaGrid offers the only two-tiered backup storage approach with a non-network-facing tier (tiered air gap), delayed deletes, and immutable objects to recover from ransomware attacks.
- Encryption: ExaGrid offers FIPS 140-2 Validated hardware-based disk encryption on all SEC models. Self-encrypting hard disks with RAID controller-based key management and access control secures your data during the storage process. Optional boot protection is also supported on all SEC models, requiring entry of a password on the system console during system boot. This separate password is used to decrypt the drive‘s data, so if this password is not known, then the server will not boot.
- Securing Data on the WAN: Replication of deduplicated backup data can be encrypted when transferred between ExaGrid sites using 256-bit AES, which is a FIPS PUB 140-2 Approved Security Function. This eliminates the need for a VPN to perform encryption across the WAN.
- Role-Based Access Control using local or Active Directory credentials and Admin and Security Officer roles are fully compartmentalized:
- Backup Operator role for day-to-day operations has limitations such as no deletion of shares
- Security Officer role protects sensitive data management and required to approve any changes to the Retention Time-Lock policy, and to approve the viewing of or changes to root access
- Admin role is like a Linux super-user – allowed to do any administrative operation (limited users given this role) Admins cannot complete sensitive data management action (such as deleting data/shares) without the Security Officer’s approval
- Adding these roles to users can only be done by a user that already has the role – so a rogue admin cannot bypass Security Officer approval of sensitive data management actions
- Key operations require Security Officer approval to protect against internal threats, such as share deletes and de-replication (when a rogue admin turns off replication to remote site)
- Two-Factor Authentication (2FA) can be required for any user (local or Active Directory) using any industry-standard OAUTH-TOTP application. 2FA is turned on by default is for both the Admin and Security Officer roles and any login without 2FA will create a warning prompt and an alarm for greater security.
- TLS Certificates/Secured HTTPS: ExaGrid software is managed through a web interface and will, by default, accept connections from a web browser on both ports 80 (HTTP) and 443 (HTTPS). ExaGrid software supports disabling HTTP for environments that require HTTPS (secure) only. When using HTTPS, ExaGrid’s certificate can be added to web browsers, or a user’s certificates can be installed onto ExaGrid servers via the web interface or provided by a SCEP server.
- Secure Protocols/IP Whitelists:
- Common Internet File System (CIFS) – SMBv2, SMBv3
- Network File System (NFS) – Versions 3 and 4
- Veeam Data Mover – SSH for command and control and Veeam-specific protocol for data movement over TCP
- Veritas OpenStorage Technology protocol (OST) – ExaGrid specific protocol over TCP
- Oracle RMAN channels using CIFS or NFS
- SSH Key Support: Although access via SSH is not necessary for user functions, some support operations can only be provided over SSH. ExaGrid secures SSH by allowing it to be disabled, allowing access via randomly generated passwords, or customer-supplied passwords, or only SSH key pairs.
- Comprehensive Monitoring: ExaGrid servers deliver data to ExaGrid Support (phone home) using both health reporting and alerting. Health reporting includes statistics data for trending on a daily basis and automated analysis. Data is stored on secure ExaGrid servers with trending databases used to determine the overall health over time. Health reports are sent to ExaGrid using FTP by default, but can be sent using e-mail with some decrease in the depth of analysis. Alerts are momentary notification that could indicate actionable events, including hardware failures, communications issues, potential misconfiguration, etc. ExaGrid Support promptly receives these alerts via e-mail from ExaGrid Support servers.
For CIFS and Veeam Data Mover, AD integration allows using domain credentials for share and management GUI access control (authentication and authorization). For CIFS, additional access control is provided via an IP whitelist. For NFS, and OST protocols, access control to backup data is controlled by an IP whitelist. For each share, at least one IP address/mask pair is provided, with either multiple pairs or subnet mask used to broaden access. It is recommended that only the backup servers that regularly access a share are placed in a share’s IP whitelist.
For Veeam shares using the Veeam Data Mover, access control is provided by username and password credentials entered into both the Veeam and ExaGrid configuration. These can be AD credentials, or local users configured on the ExaGrid site. The Veeam Data Mover is automatically installed from the Veeam server onto the ExaGrid server over SSH. The Veeam Data Mover runs in an isolated environment on the ExaGrid server which limits system access, has no root privileges, and runs only when activated by Veeam operations.

